- Tunnelblick For Android Emulator
- Tunnelblick For Android Apk
- Tunnelblick For Android Free
- Tunnelblick For Android Phone
The service is also compatible with 3rd party apps (OpenVPN Connect/for Android, Tunnelblick, WireGuard, StrongSwan and more. How many devices can be used at the same time with an account? Up to 12 simultaneous connections: 6 using OpenVPN/IPsec + 6 using WireGuard. Tunnelblick is not available for Android Tablet but there is one alternative with similar functionality. The most popular Android Tablet alternative is OpenVPN, which is both free and Open Source. If that doesn't work for you, our users have ranked 16 alternatives to Tunnelblick, but unfortunately only one is available for Android Tablet. Tunnelblick Alternatives for Windows. Tunnelblick is not available for Windows but there are some alternatives that runs on Windows with similar functionality. The most popular Windows alternative is OpenVPN, which is both free and Open Source. If that doesn't suit you, our users have ranked more than 10 alternatives to Tunnelblick and ten of.
- 1What operating systems are supported?
- 2Can I use it with my phone or tablet?
What operating systems are supported?
OpenVPN supports most operating system.
Microsoft Windows
You can download the Windows client from here: https://openvpn.net/client-connect-vpn-for-windows/. After installing the OpenVPN client, you can import the OpenVPN profile into the client.
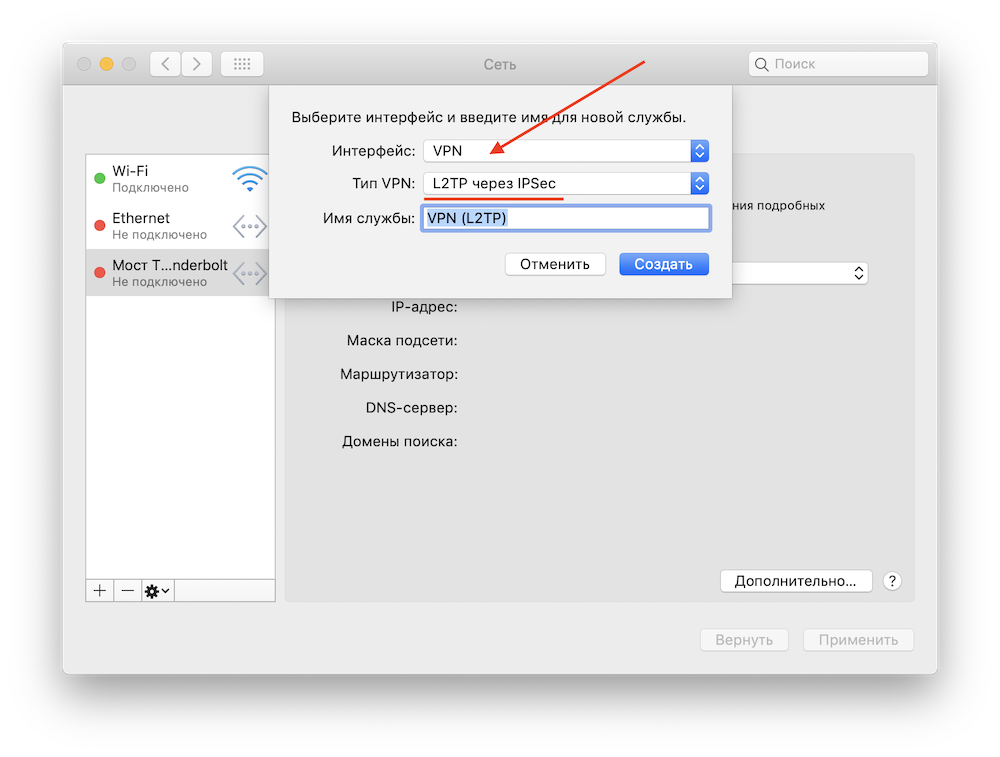
Apple Mac
For Macs, we suggest http://code.google.com/p/tunnelblick tunnelblick.
- Download and install an OpenVPN client for MacOSX
- Login to the Untangle Server, download the client config file zip and extract the files from the zip file.
- Place it in the ~/Library/Application Support/Tunnelblick/Configurations folder on the Mac.
- Run Tunnelblick by double-clicking its icon in the Applications folder.
Linux
For all other operating systems Untangle distributes a .zip with configuration and certificate files - these can be used with any OpenVPN-compatible VPN software on any operating system.
Chrome OS
Steps to install OpenVPN on Chrome OS devices:
Can I use it with my phone or tablet?
For smartphones, you'll need to install and run a VPN client that supports OpenVPN.
iOS based iPhones and iPads
For iPhones, we suggest OpenVPN Connect available on iTunes https://itunes.apple.com/us/app/openvpn-connect/id590379981?mt=8
- Install OpenVPN Connect app on your iPhone or iPad.
- Login to the Untangle Server, download the client config file by selecting 'client's configuration zip for other OSs'.
- Unzip the config file.
- Open iTunes and select the .ovpn, .crt, and .key files from the config zip to add to the app on your iPhone or iPad.
Android Based Phones
OpenVPN for Android 4.0+ is available for connecting to Untangle OpenVPN. Detailed instructions from our forum contributor WebFool. http://forums.untangle.com/openvpn/30472-openvpn-android-4-0-a.html
- Download/Install Openvpn for Android on your android unit.
- Then download the Openvpn Configuration files from the Untangle Unit.
- Unzip them and copy them to the Phone/SDcard.
- Now Open 'Openvpn for Android'
- Click 'All your precious VPNs'
- In the top right corner Click on the folder.
- Browse to the folder where you have the OpenVPN .Conf file. Click on the file and hit Select
- Then in the top right corner hit the little Floppy disc Icon to save the import.
- Now you should see 'imported profile' click on it to connect to the tunnel.
With OpenVPN, can I force all network traffic through the VPN tunnel?
Yes, you can run 'Full Tunnel' which forces all internet-bound traffic to go through the VPN and out the Untangle on the remote end (and is subject to all Untangle filtering). If running as a 'Split Tunnel' where Full Tunnell is not checked only traffic to exported networks only will go through the VPN.
Can I still use OpenVPN if my Untangle does not have a public IP?
Sometimes Untangle is installed behind another router (typically as a bridge). You can still run OpenVPN, however you will need to make some additional changes so remote clients can connect to the server:
- Port forward UDP port 1194 from your router to the Untangle server. This will allow remote clients to connect to Untangle even though it doesn't have a public IP.
- Configure your public address in Config > Network > Hostname. This is the address in the distributed clients that remote clients and networks will attempt to connect to.
Can I use OpenVPN on both of my WAN connections?
Yes. The client chooses which WAN to connect to; the server will answer via the same WAN the client connected on. The client chooses based on your configuration of Public Address. If the Public Address fails it will then try the IPs of the WANs manually as configured in the conf file.
Is there a way to setup a password for the OpenVPN users?
Yes, if you right click on the OpenVPN icon on the client's PC there is an option for a password - please note this password is only used when launching the client.
OpenVPN connects, however I can not access anything. Why is this?
Many things could cause this issue. First verify that the hosts that you are trying to reach are exported in Exported Networks. After connecting OpenVPN, try to ping Untangle's LAN IP address (if exported), then try to bring up the UI by entering the IP in a browser. If these work your tunnel is up and operational. If you can't reach a Windows machine, verify Windows Firewall is disabled on the target machine as it will block access from non-local subnets by default. If the target machine runs another OS, verify it is either using Untangle as a gateway or the machine its using as a gateway has a static route sending the VPN Address Pool to the Untangle.
How can I restrict access to certain OpenVPN users?
By default, openvpn users can connect to any machine that the Untangle can connect to. However, routes are pushed to all the 'Exported' network automatically. Beware, nothing prevents adding remote users that have administrator access to their machines to add routes manually.
If restricting access to OpenVPN users is a concern, Firewall rules or Forward Filter Rules can be used. In the Firewall, the easiest way is to create a block rule blocking traffic when Source InterfaceOpenVPN. Above that rule create rules to allow traffic when Username is the openvpn user you want to allow to the desired locations. In this scenario openvpn traffic will be blocked into your network except for explicitly allowed traffic.
Using rules you can limit access to certain resources to only the desired remote users.
Can I create site-to-site tunnels with non-Untangle devices?
When using OpenVPN for site-to-site tunnels Untangle only supports using other Untangle boxes as endpoints. Some users have had success with DD-WRT and Tomato, but this is not supported by Untangle. If you need to connect a VPN tunnel to a non-Untangle device, we recommend using IPsec VPN.
I'm using site-to-site and my software clients can only talk to the main server. Why?
If you have both software clients on the road and site-to-site tunnels, the software clients will only be able to see your main site by default. To allow them to transit the tunnel(s) to other sites, simply add the VPN Address Pool to the Exported Hosts and Networks. After this is done, software clients will be able to reach all exported sites.
How can I allow software clients to resolve DNS over the tunnel?
To allow DNS resolution for remote clients you'll need to modify some OpenVPN settings - if Untangle is doing DNS resolution on your network, simply check Push DNS in OpenVPN Settings > Server > Groups > Group Name for any groups you want to push DNS settings to. Configure the DNS settings you would like pushed to the remote clients. You may need to use the FQDN when accessing resources across the tunnel.
How do I auto-start OpenVPN when my computer boots?
This only applies to Windows XP Pro, Vista, & Windows 7 to auto-start OpenVPN on boot:First, Navigate to C:Program FilesOpenVPNconfig. This directory will have sitename.conf, sitename.ovpn and subdirectory untangle-vpn. In this directory, identify the .ovpn file that corresponds to your site's name.
Modify OpenVPN
- Go to START > Control Panel > Administrative Tools > Services
- Right click on OpenVPN and select Properties
- Change Startup Type to Automatic
- Click OK
- Close the Services window
- Close the Administrative Tools window
- Close Control Panel
Modify Registry
- Go to Start > Run > Regedit
- Follow path down to: HKLMSOFTWAREMicrosoftWindowsCurrentVersionRun
- Locate the entry for 'openvpn-gui'
- The command reference should say: C:Program FilesOpenVPNbinopenvpn-gui.exe
- MODIFY IT TO: C:Program FilesOpenVPNbinopenvpn-gui.exe --connect sitename.ovpn. Where sitename is customized for your specific site.
- Modify the following registry value to 1: HKEY_LOCAL_MACHINESOFTWAREOpenVPN-GUIallow_service
- Exit RegEdit
When the machine restarts, the user will automatically be connected with the VPN client.
Clients are getting disconnected after 60 seconds. Why?
Did you share the same client config between multiple machines. If both are running they will conflict. When the second one connects the first is disconnected. After 60 seconds the first will reconnect and disconnect the second. This repeats endlessly. Do not share the same client config with multiple machines.
I'm setting up a new client and can't connect. Why?
Make sure that the IP that the client is connecting to is the public IP of the server, or that the traffic to that IP on port 1194 is being forwarded to your server. Also make sure you are testing from the outside. By default the Access Rules block OpenVPN clients from connecting to a server from one of its own LANs. This is to prevent clients from losing connectivity while on the local network because of a routing loop.
How do load a 9.4.x (server) remote network client zip on a 10.x Untangle (client)
9.4.2 site-to-site client zip will load on 10.x without modifications. 10.x has built-in converters to load 9.4 configuration zip files.
How do load a 10.0 and later (server) remote network client zip on a 9.4.x Untangle (client)
The directory structure of the client config zip has changed in 10.0. This means 9.4 Untangle instances will not load 10.0 and later config zip files correctly. The workaround is to modify the 10.0+ zip file to the 9.4 directory structure.
Modify OpenVPN config zip file for use on 9.4 instances
- Download client config zip from 10.0 OpenVPN server.
- Unzip the config zip.
- The directory structure is
- openvpn-<name of untangle>-config
- untangle-vpn
- untangle-<random number>.conf
- untangle-<random number>.ovpn
- key <--- rename this directory to untangle-vpn
- untangle-<random number>-<name of untangle>.crt
- untangle-<random number>-<name of untangle>.key
- untangle-<random number>-<name of untangle>-ca.crt
- untangle-vpn
- openvpn-<name of untangle>-config
- Modify untangle-<random number>.conf and untangle-<random number>.ovpn files
- Change the following lines:
- cert key/untangle-4855-FortWayne.crt
- key key/untangle-4855-FortWayne.key
- ca key/untangle-4855-FortWayne-ca.crt
- To:
- cert untangle-vpn/untangle-4855-FortWayne.crt
- key untangle-vpn/untangle-4855-FortWayne.key
- ca untangle-vpn/untangle-4855-FortWayne-ca.crt
- Change the following lines:
- Rezip the directory structure from the top untangle-vpn folder
- Import this new remote openVPN client config file to the 9.4 Untangle in VPN client mode.
1. Create Certificates and Keys
Create OpenVPN certificates and keys by following the directions here - https://firxworx.com/blog/it-devops/sys ... -on-macos/
I would suggest that one generate 4096-bit keys rather than the default 2048-bit keys. This will require changes to the vars file prior to key generation.
This will generate an ~/EasyRSA-X.Y.Z directory.
2. Create ta.key
SSH or Telnet to the DD-WRT router command line.
Run the following commands
# openvpn –-genkey –-secret ta.key
# cat ta.key
Highlight the key contents and copy to TextEdit on the Mac.
Save TextEdit ta.key file to the ~/EasyRSA-X.Y.Z/pki/private/ directory on the Mac
Delete the ta.key file on router's DD-WRT command line
# rm ta.key
3. OpenVPN Server
On the Services, VPN area of the router's DD-WRT web configuration page add the following information.
OpenVPN Server/Daemon
OpenVPN: Enable
Start Type: System
 Config as: Server
Config as: ServerServer mode: Router (TUN)
Network: (local private network that is different from your primary LAN - My primary LAN is 192.168.x.0 and I put in 10.x.y.0)
Netmask: 255.255.255.0
Port: (default is 1194, I put in 80, others like 443)
Tunnel Protocol: UDP
Encryption Cipher: AES-256 CBC
Hash Algorithm: SHA256
Advanced Options: Enable
TLS Cipher: None
LZO Compression: Yes
Redirect default Gateway: Enable
Allow Client to Client: Enable
Allow duplicate cn: Disable
Tunnel MTU setting: 1500
Tunnel UDP Fragment: Leave blank
Tunnel UDP MSS-Fix: Disable
CCD-Dir DEFAULT file: Leave empty
Client connect script: Leave empty
Static Key: Leave empty
PKCS12 Key: Leave empty
Public Server Cert: Paste the contents of the ~/EasyRSA-X.Y.Z/pki/issued/server.crt file on the Mac. Make sure it only includes lines between and including -----BEGIN CERTIFICATE-----, -----END CERTIFICATE-----
Tunnelblick For Android Emulator
CA cert: Paste the contents of ~/EasyRSA-X.Y.Z/pki/ca.crt file on the Mac. Make sure it only includes lines between and including -----BEGIN CERTIFICATE-----, -----END CERTIFICATE-----
Private Server Key: Paste the contents of the ~/EasyRSA-X.Y.Z/pki/private/server.key file found on the Mac. Make sure it only includes lines between and including -----BEGIN PRIVATE KEY-----, -----END PRIVATE KEY-----
DH PEM: Paste the contents of the ~/EasyRSA-X.Y.Z/pki/dh.pem file found on the Mac. Make sure it only includes lines between and including -----BEGIN DH PARAMETERS-----, -----END DH PARAMETERS-----
Additional Config:
push 'route 192.168.x.0 255.255.255.0'
push 'dhcp-option DNS 192.168.x.1'
TLS Auth Key: Paste the contents of the ~/EasyRSA-X.Y.Z/pki/private/ta.key file found on the Mac.
At the bottom of the web page, first click on Save, and when the page comes back, click on Apply Settings
Go to Services, Services web configuration page
Find the Additional DNSMasq Options window
Add the following statement.
interface=tun2
Click on Save, and after the page comes back click on Apply Settings
Go to Administration, Commands web page
Add the following command to the Firewall.
iptables -t nat -A POSTROUTING -o `get_wanface` -j MASQUERADE
Once you added this statement click on Save Firewall.
When the web page comes back, click on Administration, Management
At the bottom of the page click on the red Router Reboot button and reboot the router. Wait 3 minutes for the router to complete its reboot.
4. Tunnelblick on the Mac
Install Tunnelblick on the Mac
Launch Tunnelblick on the Mac.
Create a folder on your Desktop with the <session_name>. I called mine Home.
Add the following statements to TextEdit.
client
auth RSA-SHA256
cipher AES-256-CBC
auth-nocache
# Use the same setting as you are using on the server.
dev tun2
# Are we connecting to a TCP or UDP server? Use the same setting as on the server.
proto udp
tun-mtu 1500
# The hostname/IP and port of the server.
remote <internet domain of OpenVPN server> <port that was defined on the DD-WRT OpenVPN web configuration page>
resolv-retry infinite
# Most clients don't need to bind to a specific local port number.
nobind
# Try to preserve some state across restarts.
persist-key
persist-tun
# SSL/TLS parmeters
ca ca.crt
cert <client_name1>.crt
key <client_name1>.key
Tunnelblick For Android Apk
tls-auth ta.key 1# Verify server certificate by checking
# that the certicate has the nsCertType
# field set to 'server'. This is an
# important precaution to protect against
# a potential attack discussed here:
# http://openvpn.net/howto.html#mitm
# ns-cert-type server
remote-cert-tls server
# Enable compression on the VPN link.
# comp-lzo
compress lzo
# Allow me to change my IP address and/or port number (if I get a new local IP address at Starbucks).
float
Save the file with the name <session_name>.conf to the <session_name> desktop folder
Copy to the Desktop <session_name> folder:
 ~/EasyRSA-X.Y.Z/pki/private/ta.key
~/EasyRSA-X.Y.Z/pki/private/ta.key~/EasyRSA-X.Y.Z/pki/private/<client_name1>.key
~/EasyRSA-X.Y.Z/pki/issued/<client_name1>.crt
~/EasyRSA-X.Y.Z/pki/ca.crt
Once all the files are in the folder rename the <session_name> folder to <session_name>.tblk
The folder will then convert itself to a file.
Click and drag that file to the Tunnelblick icon at the top of the screen. When you see a + show up, release the click.
Add the session to ALL users of the Mac
Delete the <session_name>.tblk file from the Desktop.
Click on the Tunnelblick icon at the top of the screen on the Mac and click on VPN Details.
Highlight the <session_name>.
In the VPN Details screen click on the gear icon at the bottom left of the window.
Scroll down and click on Make Configuration Private.
Type in the Mac password when requested.
Log into a WiFi link that is not on your local LAN. For testing I use my smartphone hotspot. Click on Tunnelblick icon and click on Connect to start up VPN.

5. OpenVPN on Android
Install OpenVPN for Android (OfA) from the Play Store
Copy the following files from your Mac laptop to a USB thumb drive.
~/EasyRSA-X.Y.Z/pki/private/ta.key
~/EasyRSA-X.Y.Z/pki/private/<client_name2>.key
~/EasyRSA-X.Y.Z/pki/issued/<client_name2>.crt
~/EasyRSA-X.Y.Z/pki/ca.crt
Transfer those files to the internal storage of the Android mobile device.
Open OfA
At the top portion of the screen tap on SETTINGS
Show log window: Checked
OpenVPN 3 Core: Checked
Connect on boot: Unchecked
Reconnect on network change: Checked
Pause VPN connection after screen off: Checked
At the top right portion of the screen tap the circle plus icon
Edit the profile by taping the pencil icon to the right of its name
Go to the BASIC tab
Name the profile. I use Home
Check LZO Compression
For the CA Certificate select the path to the ca.crt file
For the Client Certificate select the path to the <client_name2>.crt file
For the Client Certificate Key select the path to the <client_name2>.key file
Go to the SERVER tab
Server Address: <internet domain of OpenVPN server>
Server Port: <port that was defined on the DD-WRT OpenVPN web configuration page>
Protocol: UDP
Proxy: None
Connect Timeout: 120
Custom Options: Unchecked
Go to the IP AND DNS tab
Pull Settings: Enabled
No local binding: Checked
Override DNS Settings by Server: Unchecked
Go to ROUTING Tab
Ignore pushed routes: Unchecked
Bypass VPN for local networks: Unchecked
IPv4
Use default Route: Checked
IPv6
Use default Route: Unchecked
Go to the AUTHENTICATION/ENCRYPTION tab
Expect TLS server certificate: Checked
Certificate Hostname Check: Checked
Remote certificate subject
RDN (common name)
-- Leave Blank --
X.509 Username Field
-- Leave Blank --
TLS Authentication/Encryption
Use TLS Authentication: Enabled
TLS Auth File: Select the path to the ta.key file
TLS Direction: 1
Encryption
Encryption Cypher: AES-256-CBC
Go to the ADVANCED tab
Client behavior
Persistent tun: Checked
Push Peer info: Unchecked
Random Host Prefix: Unchecked
Allow floating server: Checked
Payload options
Override MSS value of TCP payload: Unchecked
Tunnel MTU (mtu-mtu): Using default (1500) MTU
Custom Options
persist-key
auth SHA256
Reconnection settings
Tunnelblick For Android Free
Connection retriesUnlimited reconnection retries
Tunnelblick For Android Phone
Seconds between connections2 s
Maximum time between connection attempts
300 s
To test, turn off WiFi on phone
Exit out of OfA edit mode to main screen. Tap profile name to connect to OpenVPN server.
